This article is more than 1 year old
Enable that MF-ing MFA: 1.2 million Azure Active Directory accounts compromised every month, reckons Microsoft
'Really high number' could be fixed by using multi-factor authentication
Microsoft reckons 0.5 per cent of Azure Active Directory accounts as used by Office 365 are compromised every month.
The Window giant's director of identity security, Alex Weinert, and IT identity and access program manager Lee Walker revealed the figures at the RSA conference last month in San Francisco.
"About a half of a per cent of the enterprise accounts on our system will be compromised every month, which is a really high number. If you have an organisation of 10,000 users, 50 will be compromised each month," said Weinert.
It is an astonishing and disturbing figure. Account compromise means that a malicious actor or script has some access to internal resources, though the degree of compromise is not stated. The goal could be as simple as sending out spam or, more seriously, stealing secrets and trying to escalate access.
How do these attacks happen? About 40 per cent are what Microsoft calls password spray attacks. Attackers use a database of usernames and try logging in with statistically probable passwords, such as "123" or "p@ssw0rd". Most fail but some succeed. A further 40 per cent are password replay attacks, where attackers mine data breaches on the assumption that many people reuse passwords and enterprise passwords in non-enterprise environments. That leaves 20 per cent for other kinds of attacks like phishing.
The key point, though, is that if an account is compromised, said Weinert, "there's a 99.9 per cent chance that it did not have MFA [Multi Factor Authentication]". MFA is where at least one additional identifier is required when logging in, such as a code on an authenticator application or a text message to a mobile phone. It is also possible (and preferable) to use FIDO2 security keys, a feature now in preview for Azure AD. Even just disabling legacy authentication helps, with a 67 per cent reduction in the likelihood of compromise.
MFA is only possible with what Microsoft calls modern authentication such as OAuth 2.0. Legacy authentication asks only for username and password. Even when the credentials are sent over an encrypted connection, it is more vulnerable thanks to techniques such as those described above.
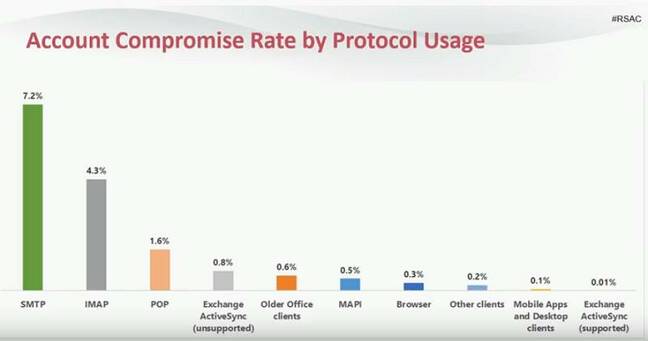
Microsoft was able to correlate account compromises with the protocols for which a user has legacy authentication enabled. If SMTP is enabled, the chance of being compromised rises to 7 per cent, RSA attendees were told.
How many users have MFA enabled? Weinert and Walker said the global adoption rate is currently around 11 per cent, accounting for the high rate of account compromise.
Disable legacy authentication, break stuff
The solution seems simple: disable legacy authentication for all users. Microsoft itself set out to do this for its own employees in September 2018. A test with a small number of users was successful so for the next phase of the rollout it disabled legacy authentication for its entire sales team, around 60,000 users. "In the middle of the night we started getting calls," the speakers said.
The problem turned out to be a telesales application which had a backend component using a single account. The login for this component used legacy authentication. The result was to break the application for everyone, causing serious business disruption, defined within the company as a "severity 1" meltdown. The new policy was rolled back.
The team started to keep a 90-day sign-in history to identify legacy authentication logins. They discovered an array of tools and utilities in use. Even the tools used to build Windows and Office depended on legacy authentication. They began the slow process of identifying the owners of these tools and working with them to update the authentication. By March 2019 they had turned off legacy authentication for 94 per cent of users, and the figure is nearer 100 per cent today. According to Weinert and Walker, who showed live monitoring graphs, Microsoft receives 1.5 million attempted legacy authentication logins every day, which are now blocked.
What's next for the rest of us?
The statistics are compelling. Disabling legacy authentication and enforcing MFA looks like a wise move for any organisation that cares about security. It is hard, though, as Microsoft's own experience shows. Fixing applications is problematic, particularly since you may not have the code. It is also a little more complex for developers, requiring token exchange in place of simply submitting username and password. Note too that the most common attacks can be prevented simply by using long, unique and unguessable passwords.
At RSA, Microsoft showed tools for disabling legacy authentication and enforcing MFA in Azure AD. The key settings are in the Conditional Access section of Azure AD, where you can set policies. A new feature in preview is to set a policy to report-only. This means that the policy is not enforced, but you get a log of sign-ins that would have failed, so you can fix them without business disruption.
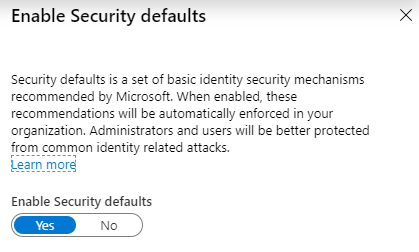
There is a snag. Conditional Access Policies are a feature of Azure AD Premium at extra cost. Many organisations therefore cannot use them. For them, Microsoft offers a feature called "security defaults", which is in the Properties section of the Azure AD dashboard. When enabled, this enforces use of the Microsoft authenticator app for iOS or Android and disables legacy authentication. This is enabled by default in Office 365 tenants created after October 22, 2019. It is all or nothing, however, and if you upgrade to using conditional access policies instead, you have to disable security defaults.
From October 2020, Microsoft is disabling legacy authentication in Exchange, which will also break some applications, but may also give organisations a nudge towards MFA.
The bottom line is that any organisation tolerating an account compromise rate of 0.5 per cent a month or more is a long way from where it should be regarding security. Disabling legacy authentication helps and enforcing MFA helps even more. ®