This article is more than 1 year old
DNS this week stands for Drowning Needed Services: Design flaw in name server system can be exploited to flood machines offline
Microsoft, BIND, Google, Cloudflare, Amazon, others fix up software or offer workarounds
A new vulnerability has been found in the design of the world's domain-name system that potentially can be exploited to flood websites off the internet.
Dubbed NXNSAttack, the flaw [PDF] can be abused to pull off a classic amplification attack: you send a small amount of specially crafted data to a DNS server, which responds by sending a lot of data to a victim's server. If you have an army of hacked PCs or devices – a botnet – at your command, and can find a DNS service that's vulnerable, you can theoretically generate enough network traffic to overwhelm a victim's system and knock it offline for all users.
Although denial-of-service attacks are a little 1990s, blasting a business off the web can lead to a loss of sales, reputation damage, and so on.
Lior Shafir and Yehuda Afek of Tel Aviv University, along with Anat Bremler-Barr of the Interdisciplinary Center, also in Israel, found the vulnerability which is illustrated below. APNIC, which oversees IP address allocation among other duties for the Asia-Pacific region, has a deep dive here.
How does it work?
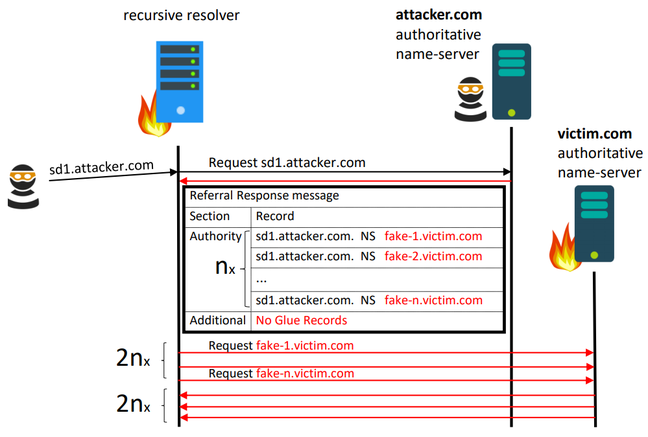
Here's a summary. You, as the attacker, need to set up a domain name like badperson.com. You want to take down victim.com's DNS servers. You connect to a recursive DNS server on the internet – such as one provided by your ISP or a cloud platform – and you ask it to resolve, say, i.am.a.badperson.com into an IP address. The recursive server contacts your DNS server for your dot.com for that information.
Your name server tells the recursive server it needs to look up another.victim.com, sad.victim.com, tragic.victim.com, fashion.victim.com, and so on, to get the answer it seeks. This message neglects to include any glue records containing IP addresses. So the recursive server – key word recursive – connects to the DNS server for victim.com and asks for the records on all those sub-domains, and the victim.com DNS server replies with error messages for the non-existent sub-domains.
As you can see, you've turned that one request into a small storm of data exchanged between the recursive and the victim.com name servers. If you get a botnet to do this many times a second or minute, you can flood both of those name servers with packets, preventing legit look-ups from getting through from netizens, and the systems will appear down. According to the academics, you can perform double amplification of network traffic by extending the attack recursively. If the servers start to cache their look ups, and do not send any further packets, simply specify new and unique sub-domains.
In more technical terms, here is how the boffins explained it:
The attacker uses the authoritative that it owns to craft a response to a resolver with a referral that contains n new and nonexistent name-server names without an associated IP address, and as a result, this resolver starts the process of F new resolutions. As shown later, the maximum F can be in the range, 74 ≤ F ≤ 2·n (in BIND implementation, 2n requests to resolve the IPv4 and IPv6 addresses). When the attacker generates many such referral responses repeatedly, she gets a DDoS attack on either the resolver or on a corresponding authoritative server, with an amplification factor of O(F) packets, sometimes much larger than F.
We're told NXNSAttack can be exploited to force the transmission of as many as 1,620 times the expected number of packets from a single request. In reality, it was shown, for example, that Google DNS could be used to generate 30 times the expected packets; 48 times from Cloudflare, 204 times from Oracle's Dyn; 415 times from IBM's Quad9; and 569 times from Norton ConnectSafe.
The danger is severe enough that it got the attention of Microsoft. As the team's research went public this week, the Windows giant issued an advisory on the matter for its DNS software, suggesting people enable response rate limits.
"Microsoft is aware of a vulnerability involving packet amplification that affects Windows DNS servers," the memo stated. "An attacker who successfully exploited this vulnerability could cause the DNS Server service to become non-responsive."
The flaw is not limited to Windows servers; it's just that Microsoft isn't in the business of posting advisories for other platforms.
To mitigate the problem, the researchers suggest name servers implement an algorithm they devised dubbed Max1Fetch that reduces the storm of traffic between the DNS components involved.
The trio said they responsibly disclosed the hole well in advance of going public, and various DNS software makers have already patched, or are in the process of patching, the vulnerability – at least some of which using the Max1Fetch method. We're told the following software suppliers and service providers have fixed up their vulnerable DNS server software:
ISC BIND (CVE-2020-8616), NLnet labs Unbound (CVE-2020-12662), PowerDNS (CVE-2020-10995), CZ.NIC Knot Resolver (CVE-2020-12667), Cloudflare, Google, Amazon, Microsoft, Oracle (DYN), Verisign, IBM Quad9, and ICANN.
You should check for updates for your DNS server installation, and install them to avoid being blown over by a distributed denial-of-service attack. "If you operate your own DNS resolver, no matter what brand it is, please upgrade to the latest version now," APNIC urged. ®